
To make web3 safer for all, WalletConnect and Blowfish have joined forces to help wallets protect their users against scams, fraud, and hacks. WalletConnect’s Verify API is a security solution that helps wallet users identify malicious domains, and it does so by leveraging its domain registry and Blowfish's Dapp Security API. Blowfish enables transaction security through its comprehensive Trust & Safety platform.
Web3 has seen a surge in user activity in recent years. It’s an exciting time for users and a huge opportunity for the entire ecosystem. Users are finally exploring the web3 ecosystem built by wallet, protocol, dapp, and infrastructure builders who have been updating the web3 experience tirelessly.
Unfortunately, when users show up and money is at risk, scammers and fraudsters show up as well. The surge in Bitcoin price towards the end of 2023 saw more users entering the web3 ecosystem, but also the number of scam alerts issued to users by Blowfish increased by 270% in one month.
In this study, WalletConnect and Blowfish provide an overview of the scale of web3’s user security problem, as well as some simple steps that your business can take to protect your users and make the entire ecosystem safer.
Pinpointing the true scale of user security risks in web3 is no easy task. There are millions of on-chain users, billions in assets, and millions of distinct transactions happening every day across blockchains. Of all this activity, how much of it is fraudulent?
According to proprietary Blowfish data, 45% of all web3 project domains created in 2023 were malicious; however, analysis by Blowfish and WalletConnect found that less than 5% of web3 users engaged with these malicious domains. Nonetheless, this number is far too high.
Many of these malicious web3 project domains impersonate well-known dapps to trick users. According to Blowfish research, notable web3 brands, such as Chainlink, LayerZero, OpenSea, and Optimism can each see upwards of 100 new copycat dapps every month being visited by unsuspecting users. Brands with exciting marketing events can see as many as 500 copycat dapps in a single month. Users have a hard time figuring out what is real when they are moving fast to take advantage of an opportunity like an airdrop. See some well-executed copycat websites below with the real websites side by side for comparison.
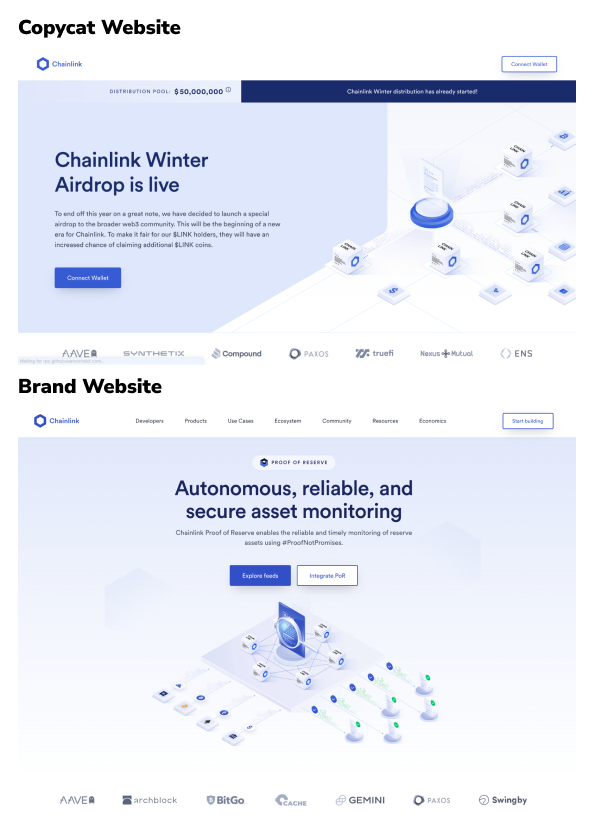
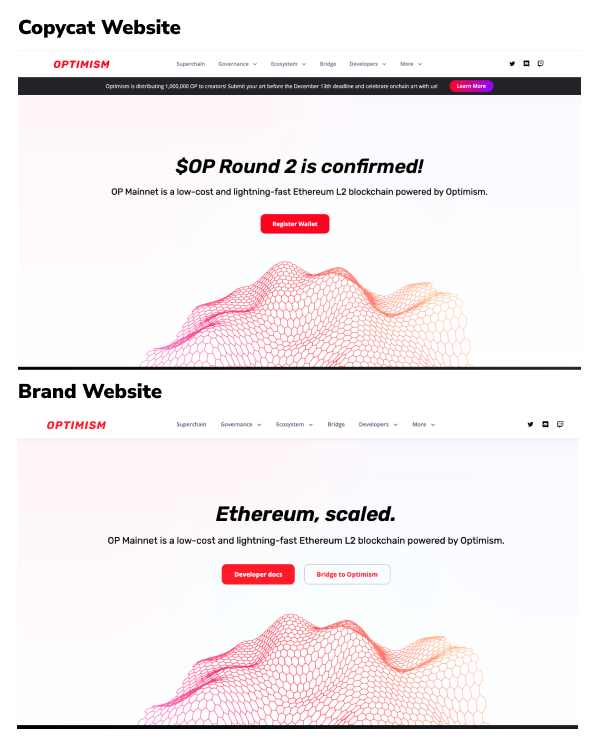
With such levels of sophistication, even experienced web3 users could easily fall victim, let alone newcomers who are dipping their toes into crypto for the first time. Copycat websites like these use convincing brand images and text to prompt users to sign transactions and messages that drain their wallet. Web3 users often find links to these dapps in Discord, Telegram, or Twitter shared by hacked real accounts, or copycat accounts that are hard to discern. These attacks can be extremely profitable for scammers, especially given the low cost to produce, so it is reasonable to expect that such copycat websites will continue to increase and spread unless wallets combat them.
On top of creating convincing malicious websites, scammers also take advantage of users on trusted dapps by creating counterfeit tokens, IP infringing NFTs, imbalanced NFT trades, or by hacking the dapp itself, to name just a few of the more common attack patterns. These attacks often have the same funnel as malicious website attacks, creating hype through Discord, Telegram, or Twitter and getting people to take action quickly. These attacks have also increased recently and Blowfish has blocked over 80,000 scam transactions in just the past month. See a well-executed attack pattern below.
Ledger’s Connect Kit, a Javascript library that implements a button allowing users to connect their Ledger device to third party dapps, was attacked in mid-December. Users visiting trusted dapps like sushi.com and using Connect Kit were asked to sign wallet draining approvals. Users lost over $600K of assets.
Wallets with Blowfish transaction security issued warnings to every user who was about to sign a malicious transaction created by the hacked Ledger Connect Kit. The warnings occurred automatically, even on a trusted dapp, due to the suspicious transaction. Wallet users were prevented from getting hurt before anyone even knew the attack was occurring. These proactive warnings saved one user over $70K.
Despite the high prevalence of scams and fraud, it has been historically challenging for wallets and dapps to build their own user protections given the complex and expensive nature of security infrastructure. Thankfully, that has changed, and protecting users has become simple and cost-effective. Below are 2 easy steps that wallets can take to protect their users today.
Identify malicious domains with WalletConnect’s Verify API: Wallets and apps can now empower their users to identify malicious domains using WalletConnect’s Verify API. When a user attempts to connect to a dapp, the wallet notifies the user if the domain in question has been verified or is potentially malicious. It’s an easy integration that realizes the web3 mantra, “Don’t trust – verify.”
Enhance Transaction Security with Blowfish: Wallets can upgrade their transaction and message signing experience with Blowfish. Using Blowfish, wallets can generate a simple preview of what’s going to occur on-chain, with an automated warning if something dangerous is detected. Simple, human-readable summaries and automated warnings delight users and provide protection against 30+ attack vectors like counterfeit tokens, IP infringing NFTs, imbalanced NFT trades, and hacked dapps that occur inside trusted applications. The integration is fast, inexpensive, and will cut down a large percentage of scams. Wallets that use both domain and transaction security services see their scam-related support tickets drop by 95%!
Web3’s potential is immense, but so are the challenges it faces from scammers and fraudsters. WalletConnect and Blowfish are committed to protecting web3 users and restoring trust in the ecosystem. If you’re sick and tired of scams hurting your users, your brand, and web3’s reputation, let’s work together.
Verify API is a layered security solution that enables wallets and apps to help users protect themselves from phishing attacks. Combining WalletConnect’s domain registry with Blowfish’s domain scanner, Verify API flags suspicious or malicious domains when the user attempts to connect to an app or sign a transaction. Over 2,000 leading web3 apps, including PancakeSwap and Snapshot, support Verify API.
Blowfish helps wallets, dapps, and infrastructure providers protect their users against scams, hacks, and mistakes across 10 blockchains. Trusted by 30 customers including WalletConnect, Exodus, and Phantom, Blowfish has helped prevent over 500K wallet-draining attacks. To learn more about Blowfish, visit www.blowfish.xyz.