
Blowfish shipped massive upgrades to transaction, message, & domain scanning in Q1. In Q2, we're going to continue shipping key upgrades as well as building a ground-breaking new product for power users.
Q1 2023 was a big quarter for Web3 security. We saw a couple large security events like the Kevin Rose NFT hack, on top of the tens of thousands of small security-related losses that nobody ever hears about on social media.
The Kevin Rose event was terrible for web3’s reputation because it highlighted how dangerous it can be to self-manage your crypto. Sign one malicious transaction or message & you could lose everything. But there was a silver lining to the event. The attention led many web3 users to start thinking about transaction security. And the great news is that transaction security tools like Blowfish can already protect users from 99% of the attacks used today.
Blowfish in 2022
Blowfish has been working on comprehensive transaction security for over a year. We help wallets, marketplaces, and applications create a safe, informative, and beautiful transaction confirmation experience for their users.
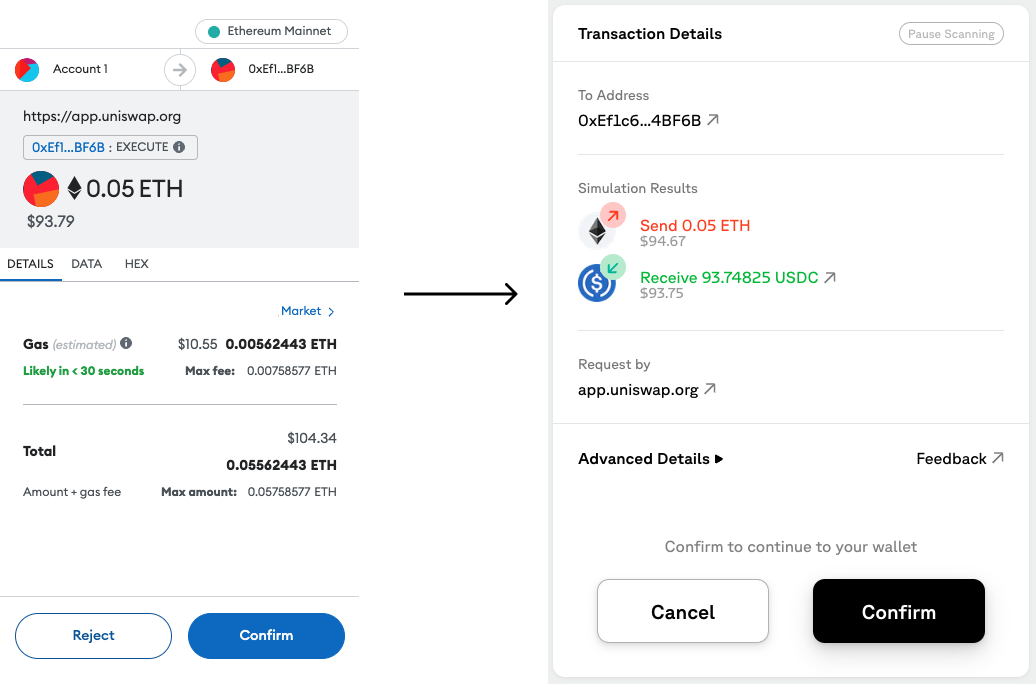
In 2022, we protected over 650K active users by scanning 200+ million transactions. We saved users tens of millions of dollars by offering:
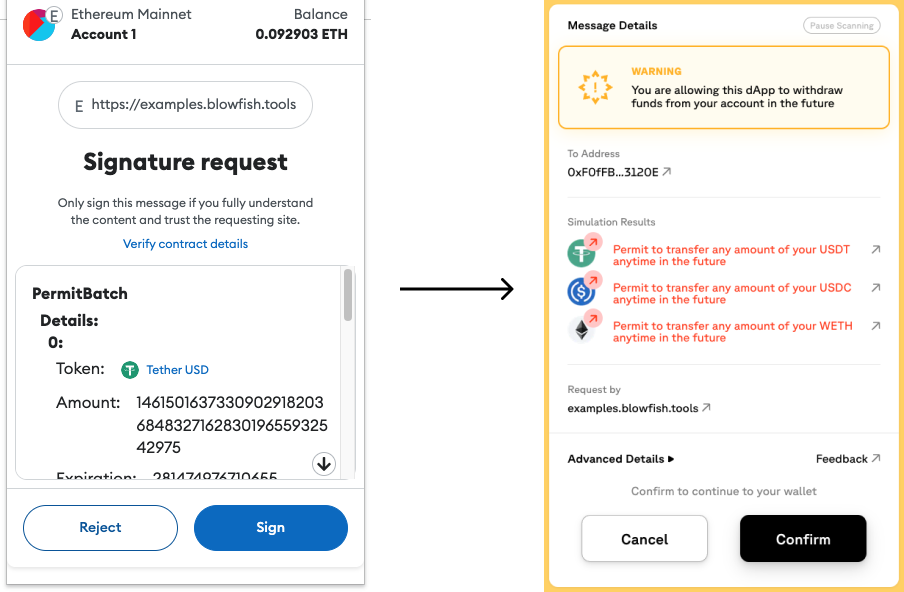
Blowfish in Q1 2023
At Blowfish, we prioritize our customers' needs and constantly strive to improve their experience. In Q1, our customers asked for product upgrades across the board, so we shipped them.

Blowfish in Q2
Blowfish is now being used to protect millions of users for Phantom, Bitski, Spot, & 20+ more teams that are integrated or integrating our security tools. Our customers rely on us to stay one step ahead of scammers, so that’s our plan. We’ll be heads down again in Q2 - listening & building. Our team has grown, so we’re excited to say that we’ll be able to ship upgrades even faster.
We have some incredibly exciting things on the Q2 roadmap:

Conclusion
We're making fast progress towards a world in which web3 users will be able to feel confident signing transactions & messages across all blockchains. In Q1, we released multiple new products as well as upgrades for all of our existing security features. In Q2, we’re excited to say that we’re going to be able to ship even more upgrades as well as something brand new for power users.
If you want to start testing our security tools today, you can grab a free API key at https://portal.blowfish.xyz/. If you would like to speak to the team directly, please reach out to [email protected].